2025 Utah Senate District 11 Voting Plan
Questions? Write to 11chooses@siv.org
Voter Experience Goals
Core Security Properties
- 1One Person, One Vote — Auditable Authentication
- 2Verifiable Results — Everyone can confirm voting was run fairly
- 3Private Voting — No one should see how voters voted
Before Voting Can Start
Voter Roll
-
Based on official State Voter File
71,526 registered voters in the district, as of March '25 -
Withheld voters: 10,925
-
Published cryptographic commitments ("merkle hash trees") for 62k active-voters list, 62k auth tokens generated, & 35k rows letter mailmerge data
What's this?
At a high-level, it allows us to prove-if-challenged, in an unforgeable way, the specific Voter Roll files used.
It also enables the ability to prove individual lines, in a privacy-protecting way, without needing to reveal the whole file.
If those challenged lines are chosen using random sampling, proving just a few dozen can imply overwhelming odds the whole file is legitimate.
Ballot
- Voting Method: Approval Voting (learn more)
- Candidates: 11chooses.com
Cryptographic Privacy Setup
This allows keeping vote selections private, even from the server. It is analogous to the "End-to-End" privacy found in Signal Messenger. More info
- Vote Privacy Protectors: 1 each from Forward Party of Utah, Center for Election Science, and SIV, + the voting server (4-of-4 key)
- Generated 4-of-4 Multiparty Encryption Key: Statements
Voting Opens
Mailers began arriving: Thurs 12/4
1. Voter receives personal vote invitation
Voter receives their vote invitation via postal mail
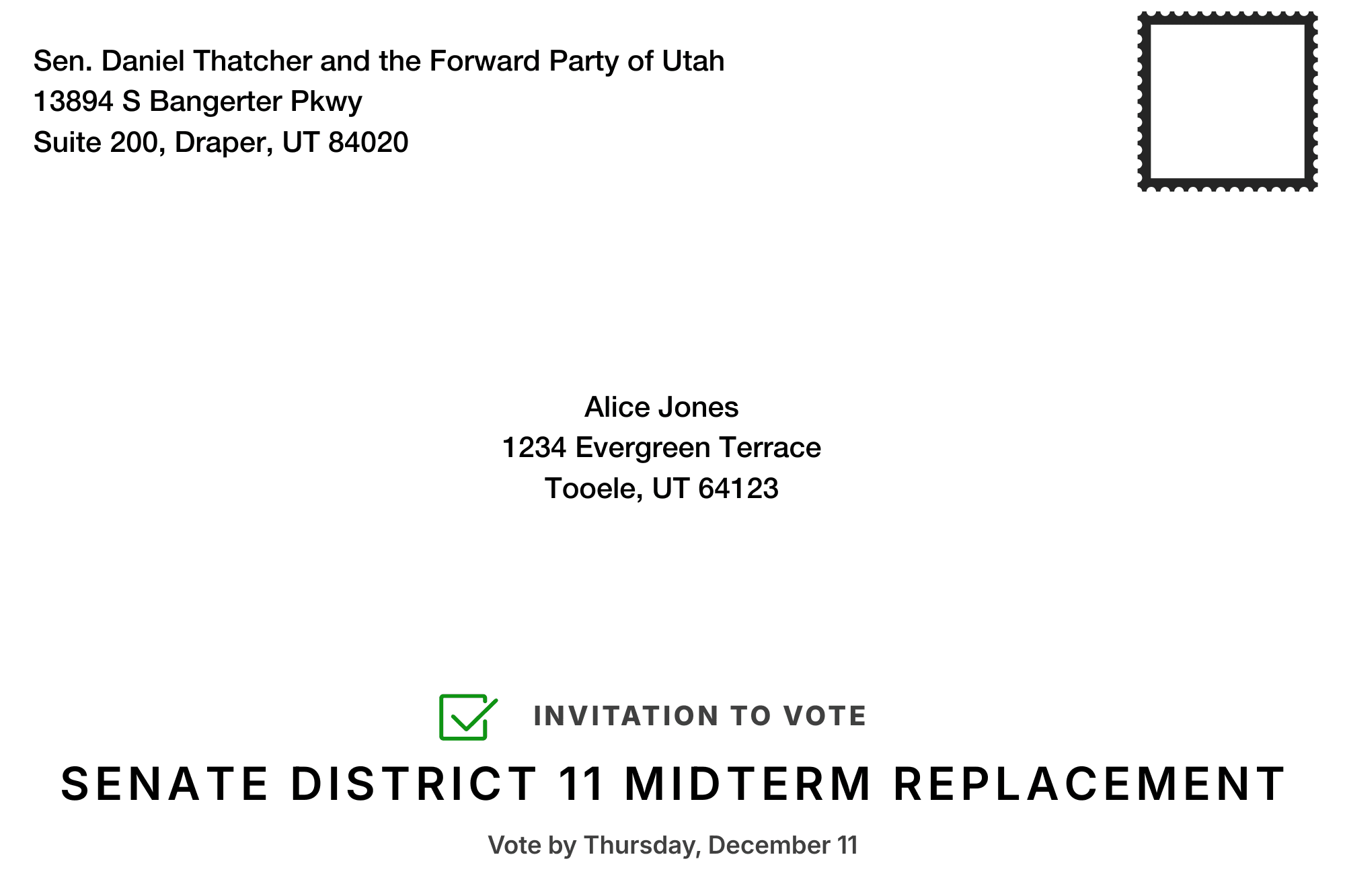
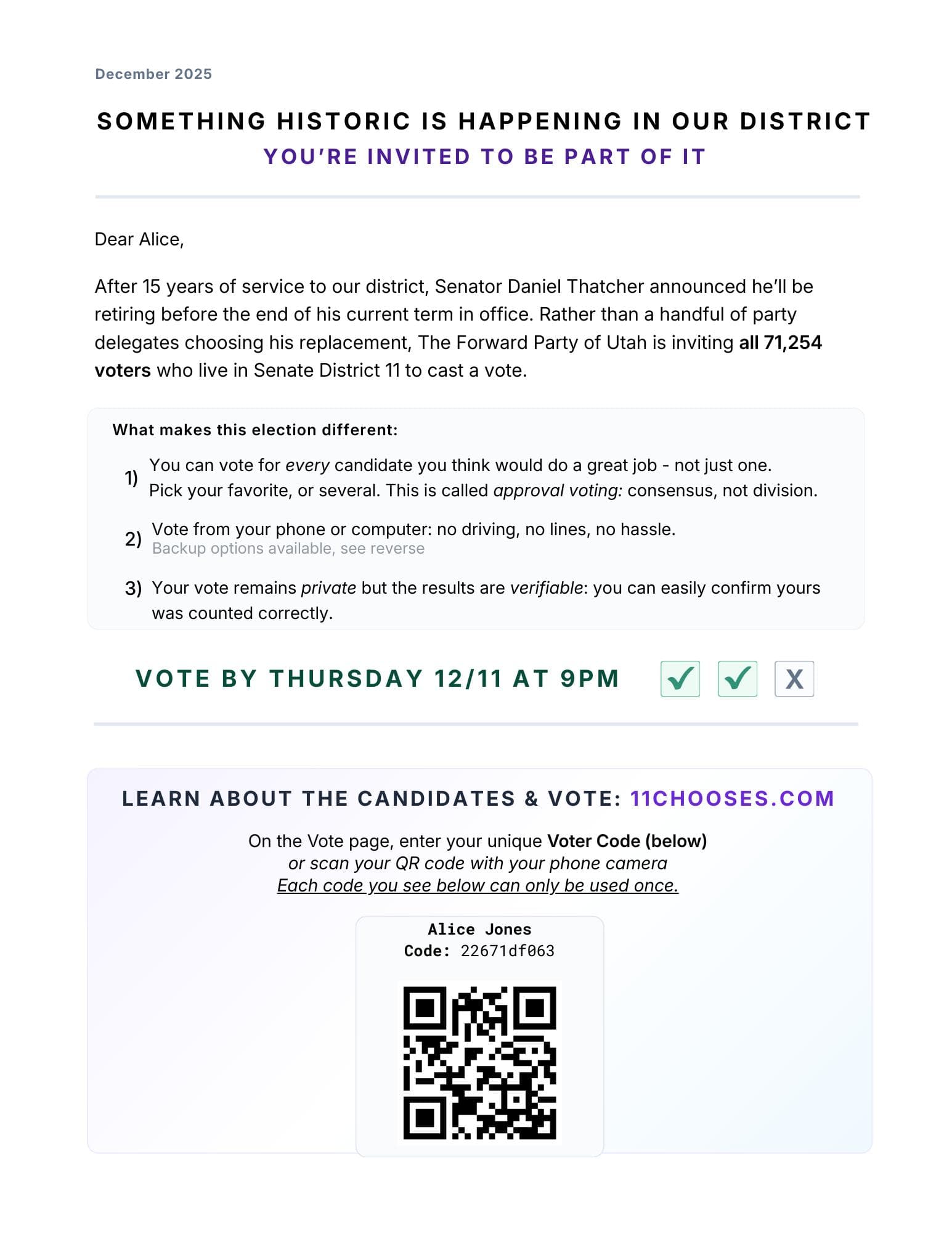

Each letter contains a unique voter credential.
- required to vote
- unique per voter
- generated by vote admin
- infeasible to guess
- can only be used once
- if necessary, vote admin can invalidate individual Voter Codes (Auth Tokens) & generate new ones
- used Voter Codes can be audited after the vote
- Remote & In-person Backup Methods available too: See Voter Authentication Options
2. Voter makes selections
Voters can enter the URL and unique Voter Code manually or scan the QR code to access the vote page.
- Voters can learn about the candidates directly on the page
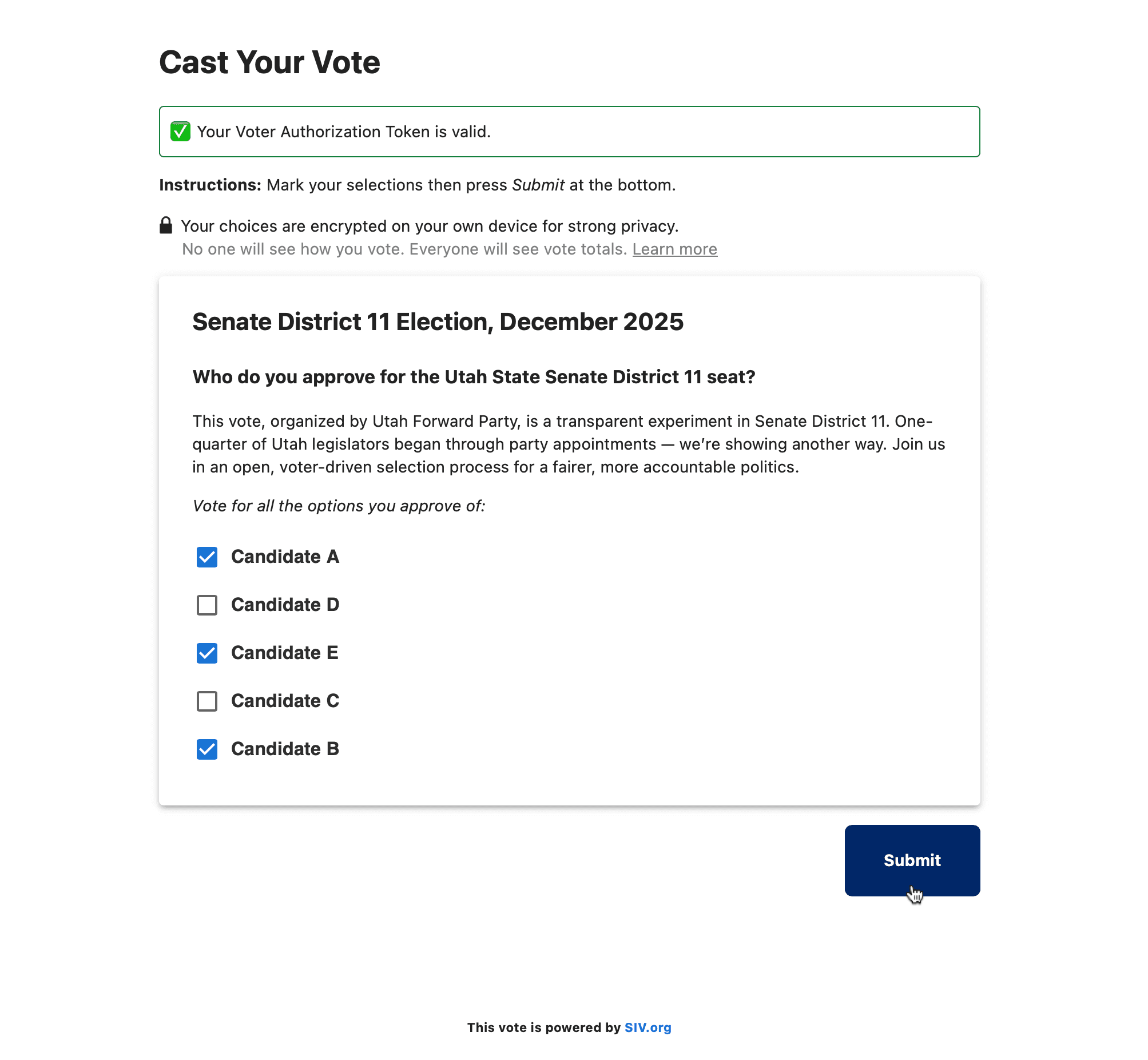
For fairness, the order of the candidates is randomized on each page load.
No app installs needed — everything runs in the browser.
3. Voter can add additional contact info
Voters are invited to add an email address for easier contact if there are issues processing their vote.
This is strictly for administrative purposes only.
Never shared or used for marketing.
4. Voter receives Vote Receipt & Verification Info
The voting software automatically stores the voter's private verification info on their own device, in the browser they use to vote.
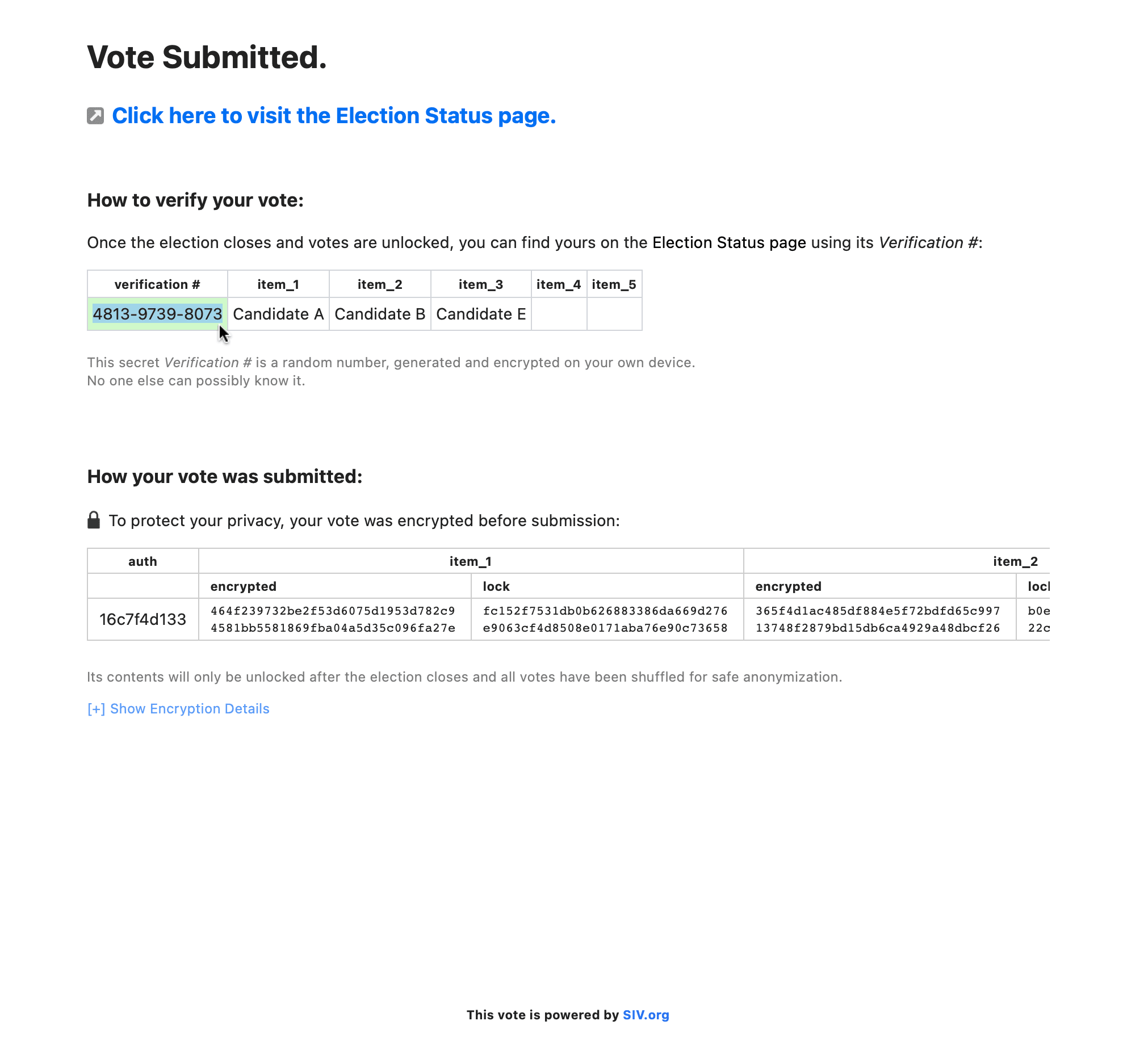
For privacy reasons, it never leaves the voter's device.
Using Provisional Ballot & Backup Auth
In case your mailer didn't arrive, was lost, or you need to cancel your first vote, you can still cast a Provisional Ballot via 11.siv.org/vote.
In person voting & support is also available: 11chooses.com/#in-person.
Read more about Authentication Options—verifying your identity and eligibility— here.
Voting Ended - Thurs Dec 11 9pm
Vote Anonymization & Tallying
Results Announced - Fri Dec 12
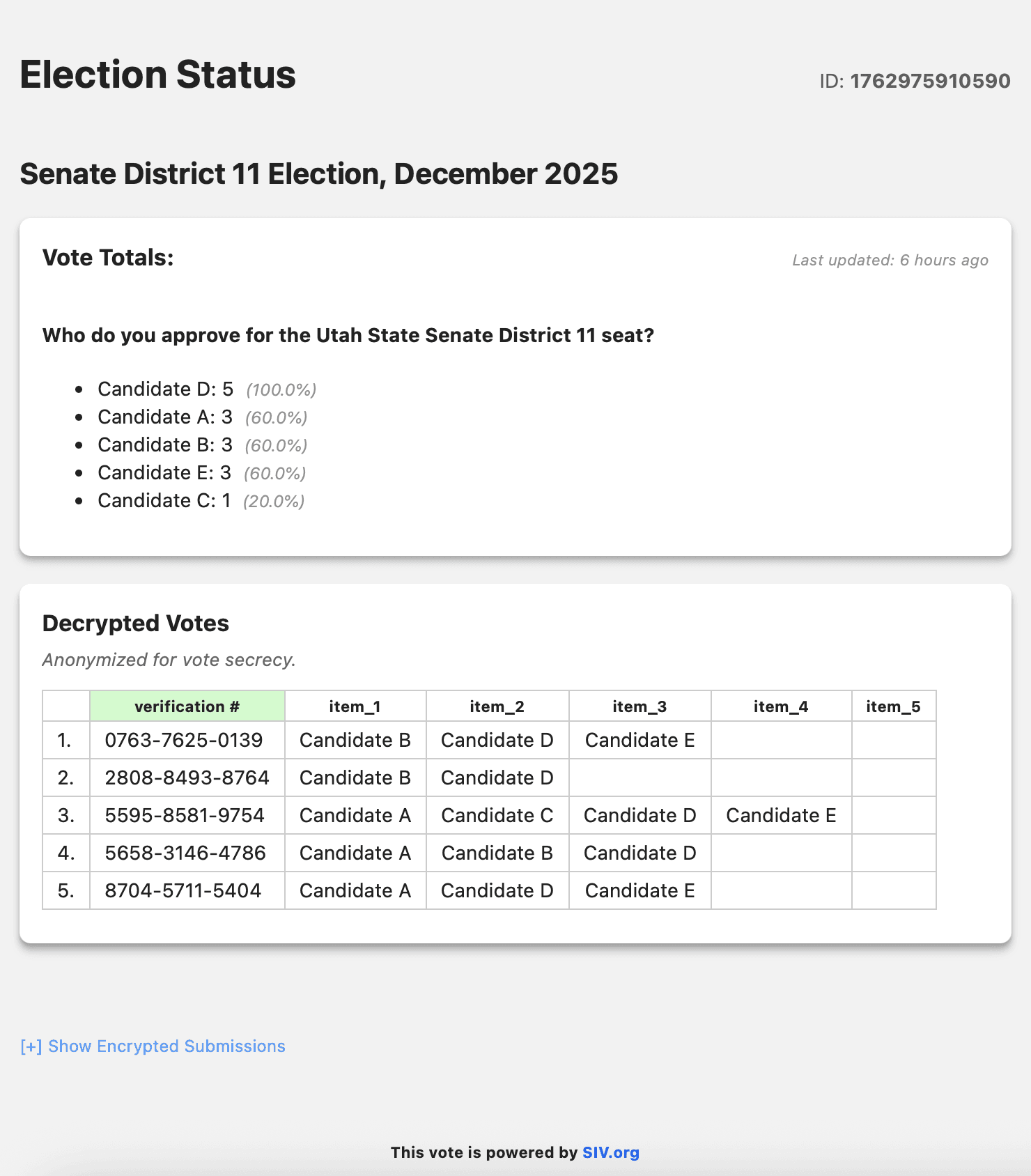
Results Published to Public Status Page
- Visit 11.siv.org/results to see the official results
Example:
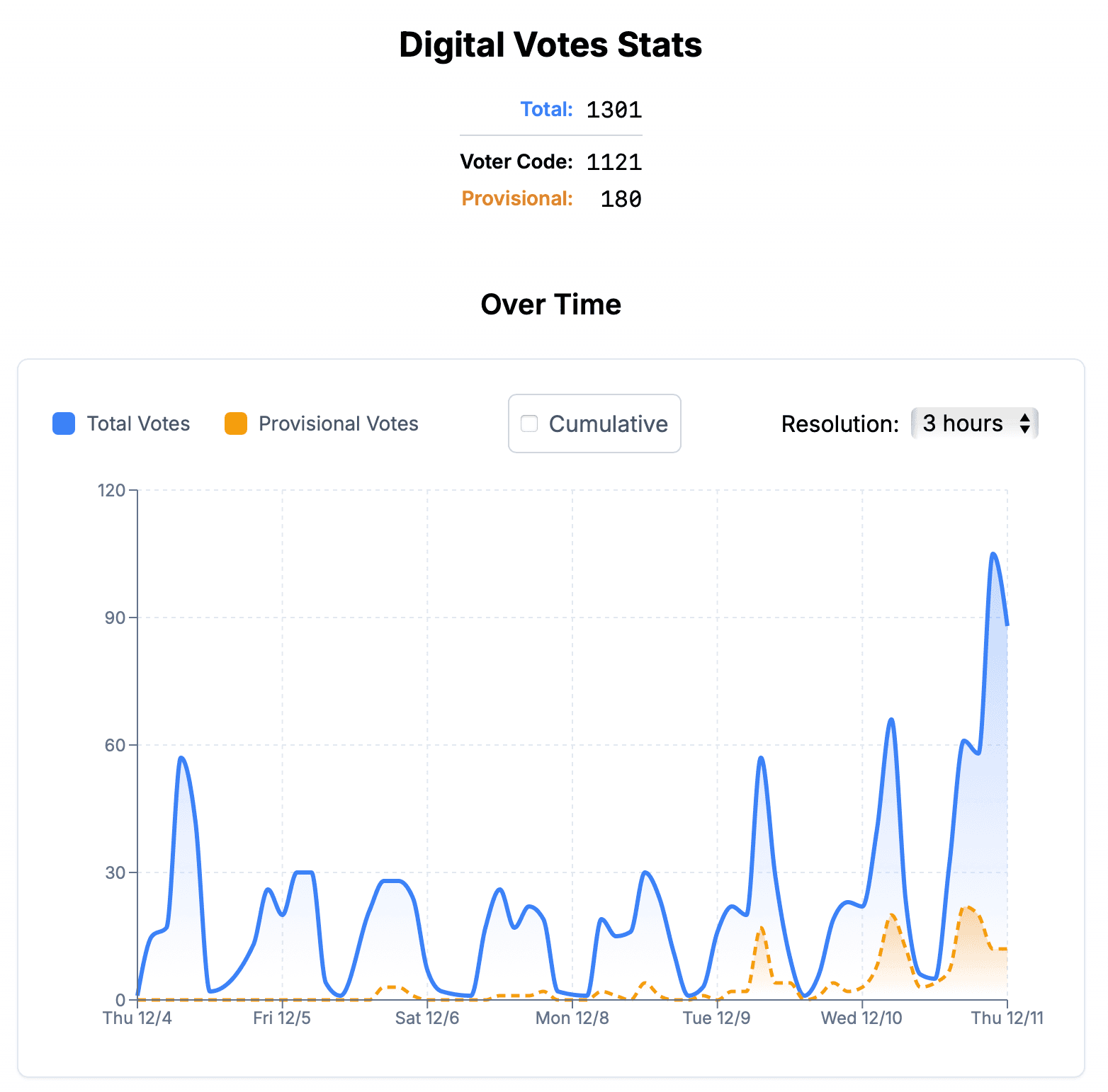
Votes-over-Time stats
- Interactive: 11.siv.org/stats
Verification Methods
Every last voter can quickly see their vote was counted as intended in the final tally
Using their unique Verification Number. More info
The full list of anonymized votes can be re-tallied by anyone, to confirm the claimed totals
The full list of anonymized votes are published one-by-one. See example image above, in Results Published section.
This allows everyone to easily re-tally the votes themselves, rather than tallying happening only behind closed doors.
The Voter Roll can be efficiently statistically audited against fake voters, stolen credentials, & other fraud
Take a random sample of voters from the voter roll, contact them to confirm they did legitimately vote— without asking them how they voted.
Voters can test their own devices for cheating malware that could have tried to secretly change their vote
Voters can use a second device to check their vote was recorded correctly. By viewing the full list of anonymized votes and looking for their Verification Number, voters can confirm their cast vote appears correctly. Voters can repeat this check on multiple devices with different malware profiles (like Android vs iPhone) for added confidence against any individual device compromise.
For full-paper checks, not requiring trust in any devices at all: The full list of votes can be printed and displayed at public locations, or brought to voters by auditors.
